安全なコラボレーションツール:2026年のプライバシーとコンプライアンスのための9つのベストオプション
2026年に最適な9つの安全なコラボレーションツールE2EE、ゼロナレッジ、監査対応が義務付けられているプラットフォームを比較してください。

安全なコラボレーションツールとは、暗号化、アクセス制御、コンプライアンス対応インフラストラクチャを通じてチームのコミュニケーションを保護すると同時に、チームが必要とするファイル共有、メッセージング、調整チームが効果的に作業できるように設計されたプラットフォームです。
コンシューマーグレードのチャットアプリや基本的なファイル共有を、データ侵害により規制上の罰金や法的責任などの対象となる組織向けに構築されたシステムに置き換えます。
安全なコラボレーションプラットフォームは、次の点で標準ツールとは根本的に異なります。
- データをエンドツーエンドで暗号化するため、サーバーにはプレーンテキストの内容は表示されません
- 監査記録とコンプライアンスレポートのすべてのアクションを記録します
- HIPAA、GDPR、FedRAMP、SOC 2 などのフレームワークをサポートします
- セルフホスティングにより、データの保存場所を完全に制御できます
- 保存ポリシー、リーガルホールド、アクセス権限を適用
そのため、患者情報について話し合う医療提供者、取引を処理する金融会社、機密データを扱う政府請負業者、特権的なコミュニケーションを管理する法務チームにとって、安全なコラボレーションが不可欠となっています。
2026年に安全なコラボレーションツールが重要な理由
安全なコラボレーションツールは、あれば便利な追加ツールではありません。機密情報を扱うあらゆる組織のベースラインインフラストラクチャになりつつあります。それぞれの要因は、攻撃の発生方法、規制の強化、チームの運営方法における実際の変化を反映しています。
1。特にコラボレーションプラットフォームを標的とする攻撃を防御します。
攻撃者は、コラボレーションツールに貴重なデータが含まれていることに気付きました。チャットログから戦略が明らかになります。共有文書には知的財産権があります。ビデオ録画は機密の議論を記録します。
IBMのデータ漏えいコスト・レポートによると、全世界のデータ漏えいの平均額は488万ドルです。この数字は、規制の厳しい業界ではさらに高くなっています。適切に暗号化されていないコラボレーションプラットフォームは、単なる生産性向上ツールではなく、攻撃対象領域でもあります。
安全なプラットフォームは、サーバーが読み取りできないデータを中継するエンドツーエンドの暗号化、ベンダーでさえアクセスできないゼロ知識アーキテクチャ、ネットワークがすでに侵害されていることを前提とした多層防御により、リスクを軽減します。
2。これによって、組織はコンプライアンス要件の正しい側に立つことができます。
HIPAA は、チームが Slack を便利だと思っても気にしません。Google Chat はすでにインストールされているため、GDPR でも例外はありません。FedRAMP は、プラットフォームを切り替えると混乱が伴うと感じるため、屈しません。
規制では、機密データの移動方法、保存場所、アクセスできるユーザー、保存期間について厳しい要件が課せられています。コンプライアンス違反のツールを使用すると、数百万人に上る罰金が科せられるほか、問題が発生したときには法的責任が課せられます。
安全なコラボレーションプラットフォームには、コンプライアンス担当者が実際に必要とする認証、監査機能、データ処理手法が備わっています。
3。データ主権の問題を解決します。
一部の組織 (政府機関、防衛関連企業、重要インフラ事業者) は、機密通信が管理外のサーバーに触れることを許可できません。データは、特定の地理的境界内、または組織が完全に所有するインフラストラクチャ上にとどまる必要があります。
セルフホストプラットフォームはこれを可能にします。エアギャップ型のデプロイメントは、外部ネットワークから完全に切り離された状態で実行され、さらに進んでいます。このレベルの制御は、すべて選択できない場所にあるベンダーのデータセンターを経由するコンシューマープラットフォームでは不可能です。
4。分散しているチームやデバイス間でのコラボレーションを確保します。
リモートワークはもはや一時的なものではありません。チームは都市、国、タイムゾーンにまたがっています。人々はホームネットワーク、コーヒーショップ、空港からつながります。彼らは会社のラップトップと並んで個人の電話を使います。
この現実は、攻撃対象領域を劇的に拡大します。安全なコラボレーションツールは敵対的なネットワークを想定し、すべてのアクセス要求を検証します。境界線はもはや存在しないため、境界線は信頼されません。
組織構築 ヒューマン AI コラボレーション ワークフローはさらに複雑になります。AI システムが通信を処理する場合、人間のユーザーと同じ、おそらくもっと厳しいセキュリティ管理が必要です。
2026年におすすめのセキュアなコラボレーションツール9選
以下のプラットフォームは、同じ問題に対して異なるアプローチを取ります。セルフホスティングとゼロ知識暗号化を優先する企業もあります。また、使い慣れた企業エコシステムにセキュリティを組み込む企業もあります。それぞれ異なる要件に適合します。
1。エレメント (マトリックス)
エレメント 分散型のエンドツーエンドの暗号化通信のためのオープンプロトコルであるMatrix上で動作します。
このアーキテクチャは、集中型プラットフォームとは動作が異なります。メッセージは送信者のデバイス上で送信前に暗号化されます。受信者のデバイス上でのみ復号化されます。中間にあるサーバーは、読み取ることができない暗号化されたペイロードを中継します。これは単なる転送中の暗号化ではなく、インフラストラクチャ自体がコンテンツにアクセスできない真のゼロ知識設計です。
フェデレーションにより、さまざまなMatrixサーバーが安全に通信できます。2 つの組織は、自社のデータの管理を放棄することなく連携できます。セルフホスティングとは、サーバーを運営し、キーを管理し、インフラストラクチャーを所有することを意味します。
セキュリティハイライト:
- すべての 1:1 会話とグループ会話でデフォルトで E2EE
- 復号できないデータを中継するゼロ知識サーバー
- セルフホスティングとエアギャップ導入オプション
- セキュリティ監査に利用できるオープンソースコード
- 暗号化を破ることなくSlack、チーム、IRCに接続するブリッジ
コラボレーション機能:
会話、音声通話、ビデオ通話、ファイル共有、スレッド、他のプラットフォームへのブリッジを整理するための部屋とスペース。
2。最も重要な
最も重要な SaaS セキュリティだけでは不十分な組織向けです。
防衛関連企業、情報機関、医療システム、原子力施設など、こうした顧客は、自分が管理するインフラストラクチャのみで動作するコラボレーションツールを必要としています。Mattermost が提供するセルフホスト型のデプロイメントでは、ユーザーが明示的に望んでいない限り、データが外部サーバーに触れることはありません。
最も機密性の高い環境では、Mattermostは外部ネットワーク接続なしでエアギャップ設置をサポートします。最近のバージョンでは、量子コンピューティングによる将来の脅威についてすでに考えている組織向けに、ポスト量子暗号法が追加されています。
セキュリティハイライト:
- クラウドへの依存が不要な完全セルフホスティング
- 転送中および保管中の暗号化、オプションの E2EE
- FedRAMP、HIPAA、GDPR コンプライアンスフレームワークがサポートされています
- きめ細かな権限と包括的な監査ログ
- 機密環境向けのエアギャップ配置
コラボレーション機能:
チャネルとスレッド、オーディオ/ビデオツールとの統合、ファイル共有、インシデント対応のためのプレイブック、ワークフローの自動化。
3。AWS ウィッカー
AWS ウィッカー ゼロ知識を真剣に受け止めています。Amazon はサービスを運営していますが、お客様のコンテンツを読み取ることはできません。
すべてのメッセージ、すべての通話、すべてのファイルが256ビットの暗号化でエンドツーエンドで暗号化されます。復号キーは受信者のデバイスにのみ存在し、Amazon のサーバーには存在せず、管理者はアクセスできず、対象受信者以外は誰も使用できません。
エフェメラルメッセージングは別のレイヤーを追加します。設定した時間枠が過ぎるとメッセージが自動的に消滅するように設定します。Burn-On-Read は視聴後すぐにコンテンツを削除します。組織は、データの保存期間を正確に制御することで、コンプライアンス保持要件とリスクの最小化とのバランスを取ります。
セキュリティハイライト:
- すべてのメッセージ、通話、ファイル、および画面共有用の256ビットE2EE
- Amazonがコンテンツにアクセスできない真のゼロ知識
- 設定可能な有効期限とバーン・オン・リード機能
- 暗号化を損なわない管理制御
- 政府機関や機密性の高い企業での使用に特化して設計されています
コラボレーション機能:
安全な部屋、ダイレクトメッセージ、音声通話とビデオ通話、ファイルと画面の共有、ポリシーベースの管理を行います。
4。ネクストクラウド・ハブ・アンド・トーク
ネクストクラウド インフラストラクチャを完全に制御できます。
ベンダーがサーバーを管理するSaaSプラットフォームとは異なり、Nextcloudはデータセンター、クラウドアカウント、ハードウェアなど、インストールした場所ならどこでも実行されます。ベンダーがデータをホストすることはないため、ベンダーがユーザーのデータに触れることはありません。
セキュリティは階層化されています。TLS はネットワーク上を移動するデータを保護します。サーバー側の暗号化は保存されたファイルを保護します。機密性の高いコンテンツの場合、クライアント側の E2EE により、自社のサーバー管理者でもデータを読み取ることができなくなります。キーはクライアントデバイスにのみ残ります。
セキュリティハイライト:
- セルフホスティングによる完全なデータ主権
- 階層型暗号化:転送時、保存時、およびオプションのクライアント側E2EE
- MLベースの異常検出によるブルートフォース対策
- パスワードレス認証と包括的な 2FA サポート
- 脆弱性に対して最大10,000ドルが支払われる有効なバグ報奨金
コラボレーション機能:
ファイルの同期と共有、リアルタイムのドキュメント編集、カレンダー、タスク管理、チャットとビデオ用のTalk、ホワイトボード。
5。シスコ・ウェベックス
シスコ・ウェベックス セキュリティをゼロトラスト問題として捉えています。
エンドツーエンドの暗号化により会議コンテンツは保護されますが、Webex はさらに強化されています。セッション全体を通して参加者の身元を検証します。攻撃者がネットワークインフラストラクチャを侵害したとしても、正当な参加者になりすましたり、暗号化された会議に侵入したりすることはできません。
暗号自体は正式に検証されています。数学的な証明により、実装が正しいことが証明されます。このレベルの厳しさは、セキュリティ障害が深刻な結果をもたらす政府機関や大企業を対象としています。
セキュリティハイライト:
- 継続的な本人確認機能を備えたE2EE
- 正式に検証された暗号実装
- インフラストラクチャの侵害を防ぐゼロトラストアーキテクチャ
- 企業および政府のコンプライアンス認証
- きめ細かな管理制御とガバナンス
コラボレーション機能:
フルビデオおよび画面共有、常設メッセージング、ホワイトボード、ウェビナー、通話、シスコデバイス統合を備えたミーティング。
6。マイクロソフトチーム
マイクロソフトチーム より広範な Microsoft 365 インフラストラクチャのセキュリティを継承します。
すでに Microsoft 365 を導入している組織の場合、Teams は既存のセキュリティ投資を拡張するため、新しい投資を必要とせずに済みます。ID 管理、アクセス制御、データ損失防止、コンプライアンス機能は、電子メール、ドキュメント、コラボレーション全体で一貫して機能します。
エンドツーエンドの暗号化は、管理者が有効にすると、1 対 1 通話で使用できます。それ以外にも、Teams は保存中も転送中も Microsoft の暗号化、広範な監査機能、組織が直面するほとんどの規制の枠組みをカバーするコンプライアンス認証を利用しています。
セキュリティハイライト:
- Microsoft 365 のセキュリティインフラストラクチャと統合されています
- すべてのコンテンツの保存時と転送中の暗号化
- 1 対 1 音声通話用のオプションの E2EE
- HIPAA、ISO 27001、SOC 1/2 認証
- 包括的な監査ログとデータガバナンスツール
コラボレーション機能:
チームチャネル、チャット、ミーティング、ファイル共有、ホワイトボード、SharePoint、OneDrive、Microsoft 365アプリとの緊密な統合。
7。Slack エンタープライズグリッド
Slack エンタープライズグリッド 規制対象業界が必要とするセキュリティ層を追加します。
重要な機能はエンタープライズキー管理です。Slack が暗号化キーを保持する代わりに、組織が暗号化キーを管理します。データへのアクセスはいつでも取り消すことができます。Slack では、管理している鍵で暗号化されたコンテンツを文字通り復号することはできません。
EKM以外にも、Enterprise Gridは、組織全体の保存ポリシー、訴訟に備えてデータを保存するリーガルホールド、電子情報開示のエクスポート、DLP統合、詳細なアクティビティを記録する監査ログなど、コンプライアンスチームが必要とするガバナンスツールを提供します。
セキュリティハイライト:
- お客様が制御する暗号化のためのエンタープライズキー管理
- ベースラインとしての保存時と転送中の暗号化
- コンプライアンスのためのリテンションポリシーとリーガルホールド
- 電子情報開示と DLP 統合機能
- SOC 2、ISO 27017、FedRAMP、HIPAA、FINRA 認証
コラボレーション機能:
チャンネル、ダイレクトメッセージ、クイックオーディオ/ビデオのためのハドル、ワークフロー、アプリ統合、外部パートナーとの共有チャンネル。
8。ズーム
ズーム 初期の批判以来、セキュリティ体制を大幅に再構築してきました。
エンドツーエンドの暗号化は、ホストで有効化されていれば利用できるようになりました。E2EE モードでは、Zoomのサーバーは復号できない暗号化されたストリームを中継します。キーを持っているのはミーティング参加者のみです。これは、機密保持がプラットフォームプロバイダーさえも除外することまで及ぶ会話にとって重要です。
ミーティング中のコントロールは、主催者にきめ細かい権限を与えます。待合室では、入室前に参加者をスクリーニングします。パスコードは認証を追加します。会議ロックは新規参加を妨げます。主催者は参加者の削除、画面共有の無効化、チャットの制限、録画の制御を行うことができます。単一障害点ではなく、多層的に保護します。
セキュリティハイライト:
- 参加者のみが復号鍵を所持するオプションのE2EE
- すべてのセッションの転送中のデフォルト暗号化
- 待合室、パスコード、会議ロック
- 共有、チャット、録音をホストがきめ細かく制御
- 継続的なセキュリティレビューと透明性報告
コラボレーション機能:
ビデオミーティング、ウェビナー、チームチャット、電話、ホワイトボード、一般的なエンタープライズツールとの統合
9。ロケット. チャット
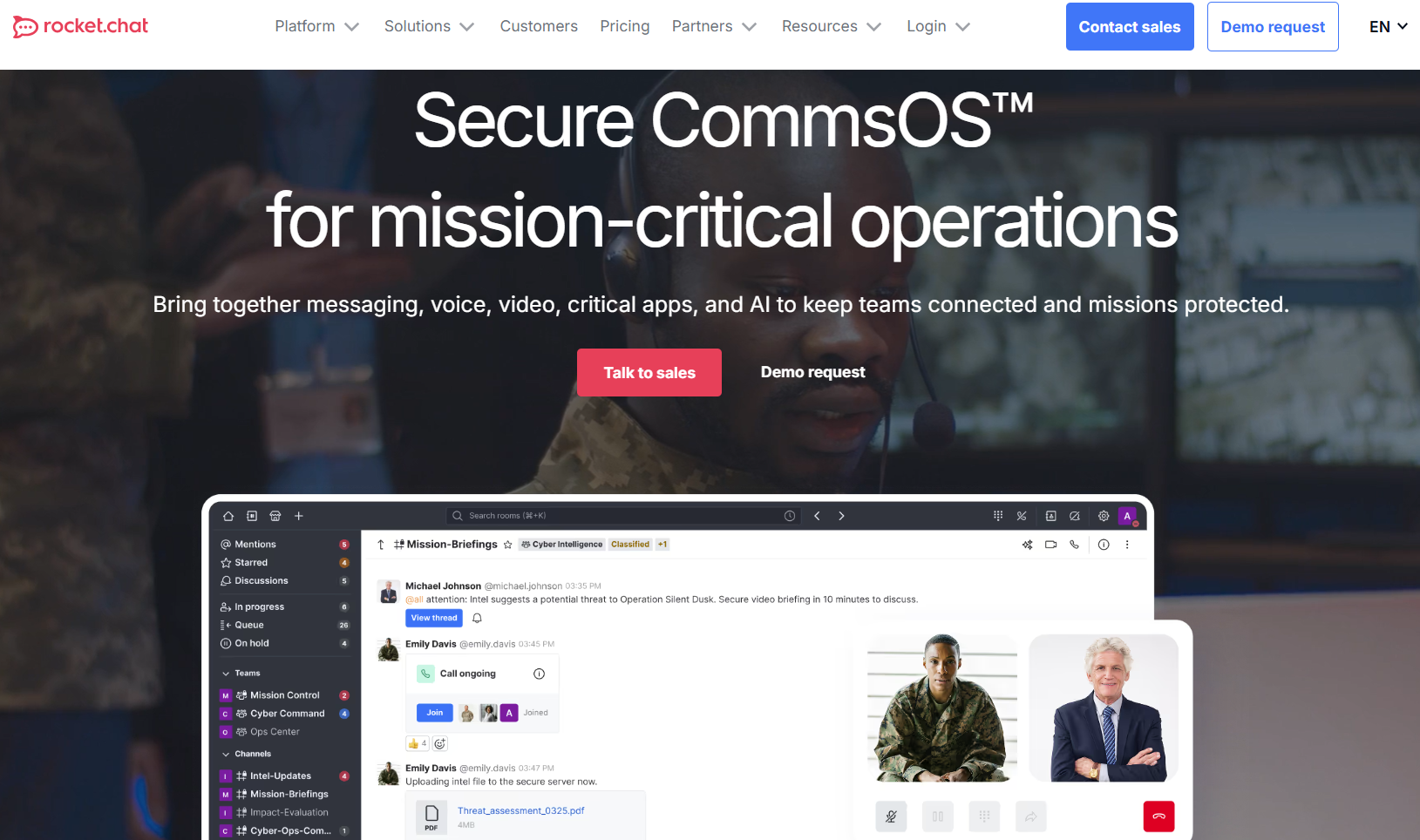
ロケット. チャット 標準のSaaSを使用できない顧客(防衛機関、情報機関、重要インフラ事業者)を対象としています。
導入オプションには、オンプレミスインストール、プライベートクラウド環境、および外部接続を一切行わない完全にエアギャップされたシステムが含まれます。サーバー、ネットワーク、暗号化キー、アクセスポリシーなど、すべてが組織によって制御されます。
エンドツーエンドの暗号化により、サーバーを実行している管理者でもメッセージの内容を読むことはできません。最近のリリースでは、特に政府や企業の高度なセキュリティ要件に合わせてこれらの機能が強化されています。
セキュリティハイライト:
- エンドポイントだけがコンテンツを読み取ることができる E2EE
- オンプレミス、プライベートクラウド、エアギャップデプロイメント
- HIPAA、GDPR、FINRA コンプライアンスサポート
- 独立したセキュリティレビューのためのオープンソース
- 防衛およびインテリジェンスのユースケースに特化して構築
コラボレーション機能:
チャネルとダイレクトメッセージ、音声とビデオ、組織間の連携、アプリ統合、ゲストアクセスの制御。
適切なツールの選択
適切な選択は、セキュリティ要件が実際にどこにあるかによって異なります。
セルフホスティングによる最大限の制御:Element、Mattermost、Nextcloud、Rocket.Chatを使用すると、すべてを独自のインフラストラクチャで実行できます。機密環境にはエアギャップオプションもあります。
マイクロソフトエコシステム:すでにMicrosoft 365に投資しているなら、Teamsは理にかなっています。セキュリティはスタック全体に一貫して適用されます。
コンプライアンスを必要とするSlack中心のチーム:EKM搭載のEnterprise Gridでは、使い慣れたワークフローを放棄することなく、顧客が制御できる暗号化機能が追加されます。
ビデオファーストコラボレーション:Webex は最も包括的な会議セキュリティを提供します。E2EE 対応の Zoom は、現在の姿勢に慣れている組織に適しています。
AWS環境:WickrはAWSと統合され、機密通信に本物のゼロ知識暗号化を提供します。
結論
機密情報を扱う組織にとって、安全なコラボレーションツールはオプションから必須へと移行しました。侵害による被害額は数百万ドルに上ります。罰金は被害をさらに悪化させます。評判を取り戻すには何年もかかる。
ここで紹介する9つのプラットフォームは、同じ問題に対するさまざまなソリューションを表しています。すべてを自分でコントロールできるセルフホスティングを優先する企業もあります。また、広範なコンプライアンス認証を取得してエンタープライズクラウドインフラストラクチャにセキュリティを組み込む企業もあります。メッセージングに焦点を当てているものもあれば、ビデオに焦点を当てているものもあれば、ファイルコラボレーションに焦点を当てているものもあります。
しかし、安全なコラボレーションは全体像の一部にすぎません。チームには、これらのプラットフォーム全体で生成された知識、暗号化されたチャットで下された意思決定、安全なチャネルで共有されるファイル、ツールに散在するコンテキストを整理する方法も必要です。 久瀬 情報をつなげることができるため、チームは導入したセキュリティ管理を犠牲にすることなく必要な情報を見つけることができます。
安全なコラボレーションに投資している組織は、進化し続ける脅威から身を守ることができるようになりました。攻撃がより巧妙になり、規制当局の忍耐力が低下するにつれて、待っている組織は増大するリスクに直面しています。


